Berltolt Brecht scholars, even more than than literary scholars in general, face
urgent challenges to their work from information technology and its legal and
institutional frameworks. Brecht's work is entangled with the law of print and
performance copyright, and with technical issues of Internet distribution, audio/visual
rendering, and long-term digital storage. Scholarship takes place inside academic and
governmental structures devoted to their own diverse agendas. This essay addresses how
scholars and other communities of readers can extract maximum benefit from available
technology, while at the same time evading the legal and less-legal snares set to
extract maximum profit from information.
To the extent that we academics can survive the political and environmental crises we
share with the rest of the world, our distinctive social function, alongside artists and
many other allies, is to resist the erosion of social commitments that are not native to
capitalism. We transmit culture, elaborate it, promote academic freedom and the free
exchange of ideas, and defend social institutions that allow these principles to
flourish. The following table lays out the minimal conditions that scholars need to do
their work, organized by access to information and the possibility of
collaboration.
Table 1. What scholars need
| Access |
Collaboration |
To primary materials To secondary literature To analytical tools
|
Among scholars In the classroom Through performance With the public Locally and remotely
|
Access means the availability of materials and tools unencumbered by burdensome fees
or institutional gate-keeping. Collaboration refers to the essentially social nature of
learning and art, which far from being "ivory tower" activities are ideally encounters
among diverse artists, performers, scholars, students, and audiences of all social
classes and bringing every conceivable intention and expectation to bear in their
artistic engagement. The key benefit conferred by the Internet and by digital
distribution is the potential to remove practical barriers to access and
collaboration.
Compatibility with these needs must be the criterion when evaluating a technology for
an academic project. Sound judgment requires an understanding of the tools available,
ranging across Web sites, discussion lists, social media, chat platforms, collaborative
online office tools, online publishing of all sorts, video conferencing, online library
holdings, online video, online teaching, online performance, analysis and visualization
of data big and small, and pattern-recognition algorithms. However, these technologies
exist within governmental, institutional, and commercial contexts that confer varying
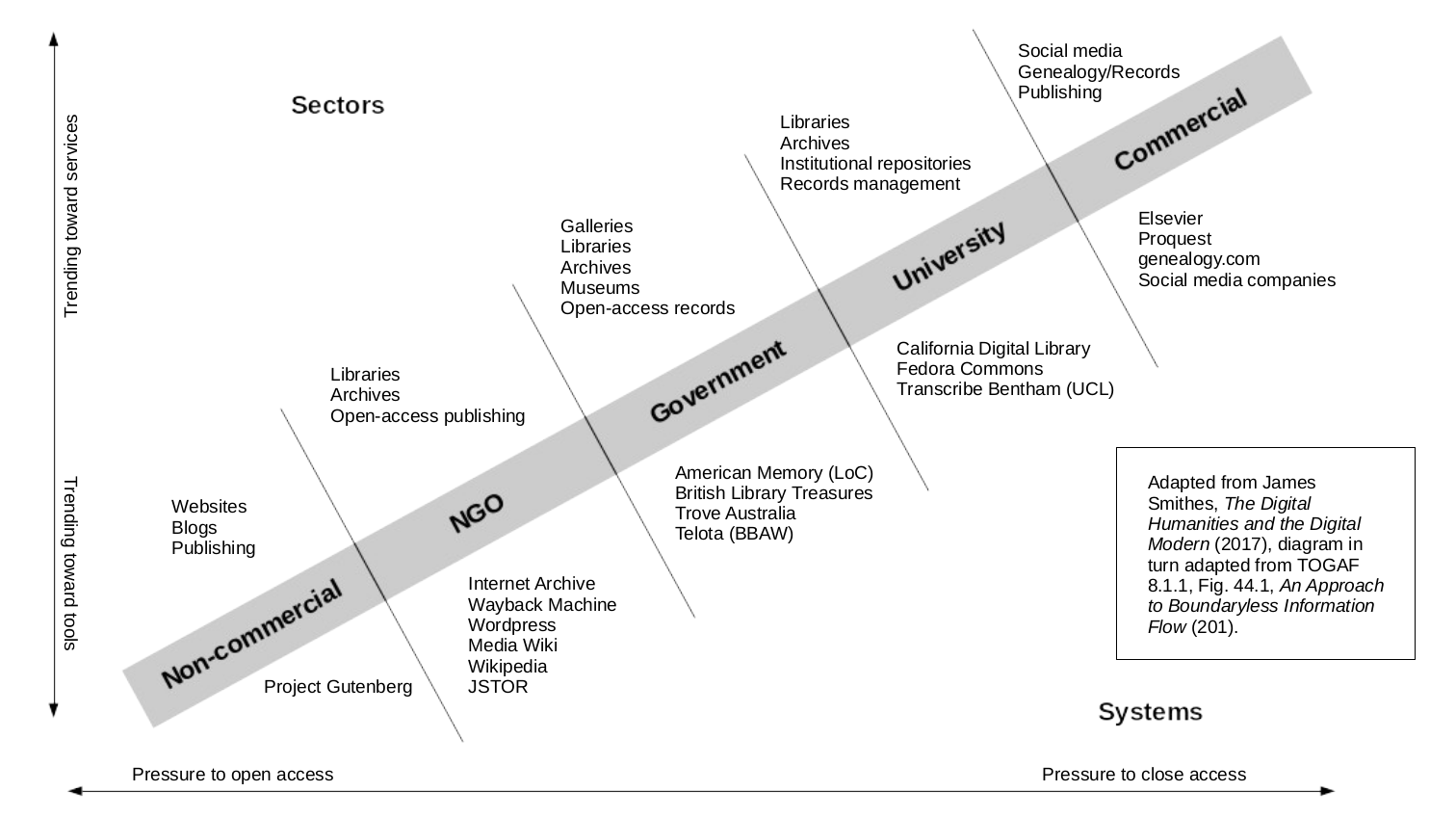
degrees of freedom and restriction on scholars. The following diagram illustrates some
of these relations.
(Smithies, 128)
Both axes in this diagram indicate degrees of control, favoring either the scholar or
someone else (e.g., a lawyer, a bureaucrat, a dean, or a corporation). The horizontal
axis measures access to information (“openness”). The vertical axis measures control by
users over the technology, ranging from freely available “tools” to contractually
restricted “services.” Each segment of the gray bar (Non-commercial, NGO, etc.) provides
typical distribution modes above the bar and specific real-world example below the bar.
At lower left, a maximum degree of both freedoms is obtained by using the open World
Wide Web to publish material unencumbered by restrictive copyright. At upper right, the
least degree of both freedoms is available to users of commercial Internet services and
publishers profiting from traditional restrictive copyright. A scholar with advanced
technical skills might choose to build custom tools and services, providing greater
freedom. A less technical scholar might contract with an NGO or business to use a
ready-made service. The choices are not crudely “freedom good, commercial bad” – all
choices involve trade-offs. The important thing is to understand what is being traded
off.
The challenges to scholarship that computer technology creates or complicates are too
numerous to list exhaustively, but they can be categorized as follows.
Copyright
The problems caused by copyright are mainly legal, not technological, but
digitization of content and potential for easy distribution over the Internet
have made the legal issues far more acute. Current legal theories are out of
step with current technology, despite all the contorted and ineffectual measures
to restrict file-copying, collectively known as “digital rights
management.”
Gating
Like copyright, physical and bureaucratic restrictions on information flow are
not new. Governments, universities, and businesses all have strong motivations
to hoard and hide knowledge. Computers, however, provide endless new
opportunities to do this for power and profit.
Technological traps
Librarians are painfully aware of how hard it is to choose a file format today
that will still be readable in 10 years. The go-go-go business culture of the
tech industry is littered with antiquated formts, dead companies, abandoned
software, and undocumented APIs that can ruin the day of anyone depending on
them.
Vendor lock-in
The technological traps aren’t just accidental. Technology companies scheme
routinely, and sometimes illegally, to make it painful or impossible for their
customers to jilt them in favor of a competitor.
In the confines of this brief paper, I offer two examples of these threats as they
have played out at the intersection of technology and creative arts.
Example 1: Services instead of things
The most lucrative business model in a data economy is one where the company owns
everything and the customer owns nothing. That way, the company has no need to
produce and sell a product, just a service, which is “licensed,” not sold. Offering
a service is almost a good as possessing a monopoly, because only the service
provider possesses it, while the customer receives an intangible that is consumed
as soon as used, and is safe from the possibility of accumulation or resale. In
cloud services, this model is called Software as a Service (SaaS).
For example, Microsoft began as a seller of boxed software—an old-fashioned
physical product. It then cut an exclusive licensing deal with IBM for preinstalled
operating system software. When cheap clones of IBM hardware grew to dominate the
personal computer market, Microsoft software remained the single common component,
leading to monopolies in operating system and productivity software (such as Office)
that endured through legal and illegal means for 20 years. This ended only when
mobile computing, and remotely offered services, began making standalone PCs and the
software running them obsolete. Seeing its pre-installed operating system monopoly
dwindle, Microsoft doubled down on its productivity business, reinventing itself as
a cloud company for “office services.” Office became Office 360, a cloud service.
You no longer own anything, and you pay a subscription fee … forever. There’s no
longer a need to tout pointless upgrades, because customers either pay the monthly
utility bill or they get cut off entirely.
Something similar happened in the music industry. Enticed by lower production
costs and promising customers improved audio quality, the record companies embraced
digital technology in the 1980s in the form of the Compact Disc. Vinyl nostalgia
notwithstanding, that format was hugely popular, and within a decade, every analog
music recording with potential for future sales had been remastered to CD. Yet the
industry made committed a tactical error: CDs were unencrypted. The ease of perfect
duplication that made digital audio technologically attractive also, inevitably,
made it convenient for file-sharers. The industry fought file-sharing for years by
suing its own customers, but their profits plummeted. Then Apple iTunes introduced
license-based, rather than product-based sales, a business model in turn overtaken
by product-free streaming services. The result, still evolving, might be called
Music as a Service, improving over prehistoric broadcast radio by directly charging
money for every listen.
What does this have to do with humanities scholarship? Suppose a project such as a
critical edition is entirely unencumbered by copyright. The researchers contract
with a software provider to host their data on the web and provide online editing
and collaboration tools. Alas, the company goes out of business after five years,
and their database structures disappear with them, while their server software is
sold to Uber, which sees vague but huge business opportunities. The researchers
consult the contract, and learn that they now possess nothing but the original data
they provided, and that only because they made a backup. (But now I stray into pure
fantasy.)
Example 2: James Joyce's Ulysses
Enough fantasy; now for a literary nightmare. In the 1970s and 80s, a team of
German textual scholars led by Hans Walter Gabler assembled an ambitious new
computer-aided edition of James Joyce’s 1922 novel Ulysses. The
textual history of Ulysses had been vexed from the start by
Joyce’s slow and accretive style of composition. On every typescript or proof
returned to him, he crammed the margins full with revisions in a barely legible
hand, leading to copy errors at every stage, including some by Joyce himself. The
trade editions inherited a famously corrupt original text, and all of them added
still more errors of their own. The following galley proof of the the novel's final
page gives a sense of the problem.
(Joyce, Ulysses Placards, "Penelope," E fin [3 of
5])
Gabler and his team attacked this challenge by creating a “synoptic edition”, a
genetic text that collated and compared every extant note, manuscript, typescript,
galley proof, edition, and errata list that Joyce's authorial hand had touched.
After these materials were digitized and appropriately tagged, the team used custom
software to generate a continuous authoritative text as well as a “synoptic” text
that displayed the revision history. The continuous text, which Gabler touted as
containing more than 5000 corrections (Gabler, vii), was published as a new trade
edition by Random House in 1986. The image below from the synoptic edition shows the
genetic text on the left and the matching continuous text on the right.
(Joyce, Ulysses: A Critical and Synoptic Edition, Vol. 1, pp.
448-349)
The Gabler edition was controversial for its methodology, accuracy, editorial
decisions, and motivations. Its detractors suggested, not unreasonably, that
financial backing from the Joyce estate and Random House was aimed at establishing
lucrative new copyrights extending well into the next century. Certainly Random
House stood to corner the worldwide market for the novel, and after a fashion it
succeeded—at the cost of trashing Gabler's reputation and harming the entire field
of Joyce studies. For the publisher, the 5000 corrections in Gabler's Ulysses were
just a marketing bauble. After rancorous debate by textual scholars in the pages of
the New York Review of Books (Kidd, "The Scandal of Ulysses"; Staley, "The Continuing Scandal of Ulysses"; Rossman, "The New Ulysses: The Hidden Controversy"; Groden,
"Ulysses Update"; etc.), and after WW Norton
jumped in to promise another, competing correction of
Ulysses, Random House abandoned the Gabler edition and
returned to selling reprints of its flawed 1961 edition.
Looking back at that pre-Web era, my saddest reflection is that Gabler's project
simply ended once financial support ended. The data and software never saw the light
of day. Whatever its flaws, the project was a groundbreaking achievement in digital
humanities that could have been refined and built upon. Today, if unencumbered by
copyright, it would be an ideal candidate for massively distributed scholarly
collaboration of a kind unimaginable in the 1980s. But it is encumbered by
copyright. If viewed as “a derivative work made for hire by Hans Walter Gabler for
the Estate of James Joyce, the U.S. copyright in the edition would last for 95 years
from the year of first publication, or until 1 January 2080” (Saint-Amour,
756).
When I moved out of academic work and into the computer industry, one of the first
things I learned was that software has been an "intellectual property" battleground.
Unlike artifacts of a natural language, such as a play by Brecht, a computer program has
two aspects: the source code, which can be written and read by trained human beings, and
machine code, which is read and acted upon by computer hardware. As a result, software
lends itself to the creation of artificial scarcity. If you hide the source code from
customers, giving them only the "compiled" machine code, you can prevent them from
studying how it works, modifying it, and creating new value from it. This constitutes a
business model.
Software with more or less freely available source code predates this model. Early
programmer culture emerged from military and academic environments that were insulated
from market incentives. The commercial computer industry of the 1950s and 60s concerned
itself with selling super-expensive hardware to governments and corporations, giving
little thought to software itself an object of value. The words, symbols, ideas, and
algorithms of software became commoditized only in the 1970s and 80s after computers
grew more affordable and interchangeable. Once computer code was understood as something
worth locking away, companies like Microsoft turned software sales into big business.
And so it came to pass that proprietary software development replaced collaborative
development with a regime of patents, trade secrets, and copyright restrictions.
When programmers accustomed to freely acquiring, studying, distributing, and modifying
source code found themselves locked out by licensing agreements, some of them, led by
MIT researcher Richard Stallman, came up with a creative solution. First of all, and
rather insanely, they rewrote from scratch the dominant server software of the day,
Unix, producing their own copyrightable code. Second, and rather brilliantly, they
hacked the copyright system into what is waggishly referred to as
copyleft, and more formally as free or open-source software.
Whereas traditional application of copyright prevents non-owners from copying and
redistributing materials, copyleft allows anyone to copy, modify, and redistribute, but
not to hoard the improvements they make. The primary goal was to protect the freedom of
programmers to program collaboratively. The first and classic example of this model is
the GNU General Public License, or GPL, under which Stallman and his colleagues licensed
their new software. Stallman grounded his copyleft philosophy in the “four freedoms”,
which have an obvious affinity to the access and collaboration required for scholarly
work.
Richard Stallman's Four Freedoms
A program is free software if the program's users have the four essential
freedoms:
Freedom to run the program as you wish, for any purpose.
Freedom to study how the program works, and change it so it does your
computing as you wish.
Freedom to redistribute copies so you can help others.
Freedom to distribute copies of your modified versions to others. By doing
this you can give the whole community a chance to benefit from your
changes.
(Stallman, "What is
free software?")
Importantly, the meaning of "free" in the term "free software" has to do with freedom
of action, not price. Stallman's freedoms do not preclude the sale of software or of
technical support for it, but neither do they enshrine profit as a preeminent value.
Money can be made directly from free software only if its informational content is fully
disclosed and remains open to unrestricted redistribution and modification.
The copyleft software model was so successful that today, 30 years after the GNU GPL
was introduced, it protects the main software powering the Internet (GNU Linux) as well
as the world's most popular mobile operating system (the Linux offshoot Android). This
success derives from the paradox of free software's profitability. Commercial software
giants such as Google, Amazon, Microsoft, and IBM contribute funding and expertise to
the ongoing development of Linux because broad collaboration ultimately spares more
costs than it consumes.
While the GPL is intended to protect computer programs, the reinterpretation of
copyright through the lens of the four freedoms has been generalized to cover a much
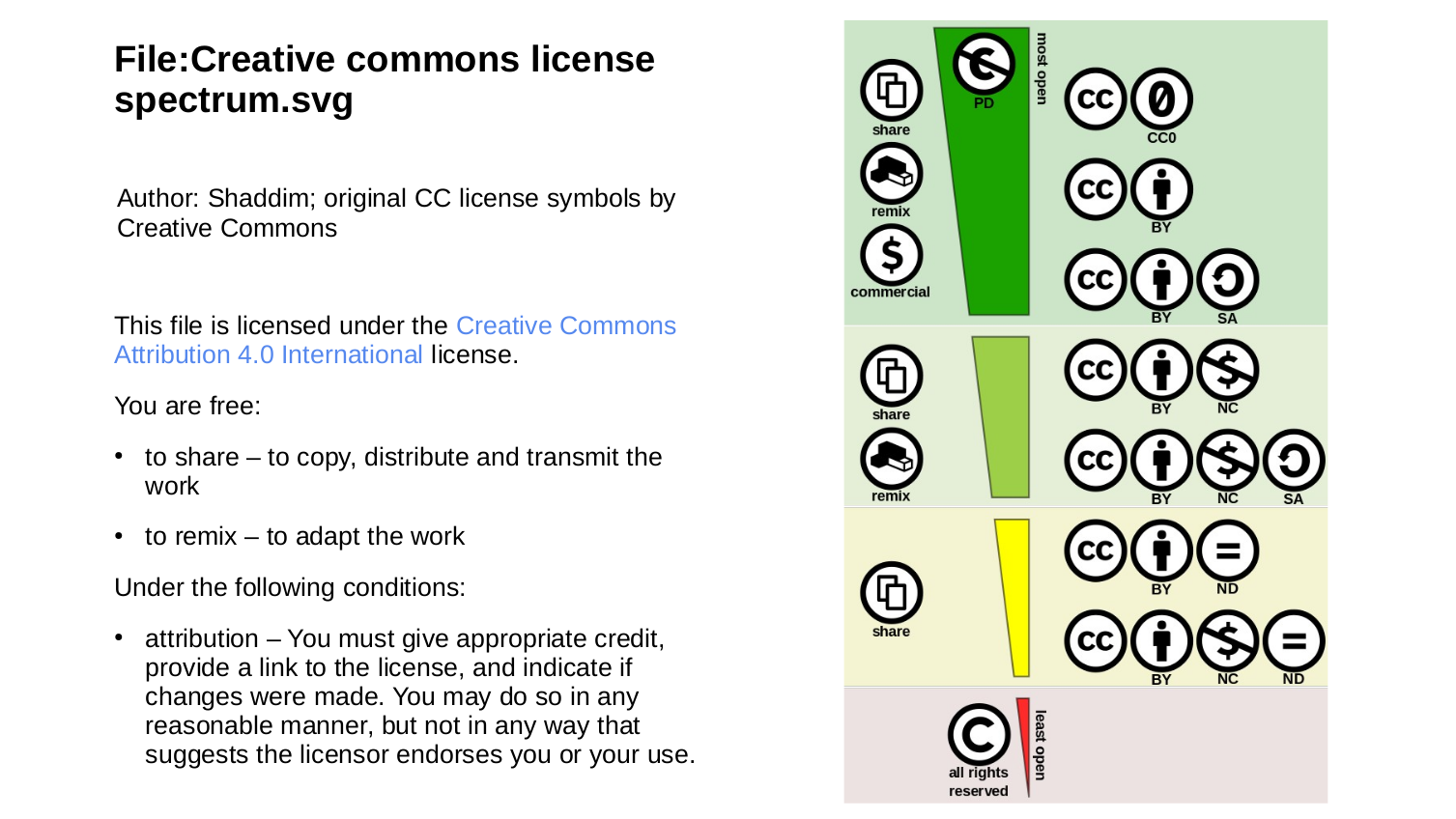
wider range of intellectual property scenarios. Most notably, the Creative Commons project provides a
comprehensive framework of licenses ranging from traditionally restrictive copyright to
completely unrestricted distribution. The image below is a representation of the various
Creative Commons licensing icons, and the accompanying text is Wikimedia's licensing
statement for the image, itself licensed under Creative Commons. This particular license
confers rights on the user that are approximately equivalent to those provided by the
GPL.
(Wikimedia, File:
Creative commons license spectrum.svg)
Applied to academic publishing, copyleft licenses can protect new material that
scholars create, including new editions of primary literature that has fallen into the
public domain. As the Brecht copyrights approach expiration, the Brecht estate and its
allied publishers will attempt to create new editions with new copyrights that will
guarantee profit and control for another century. They require scholarly labor to
achieve this. I urge Brechtian to drive a hard bargain with publishers and universities.
Don’t contribute to projects that lock away intellectual work. Use copyleft to build a
distributed, high-participation, computer-aided future of open scholarship.
The following table maps the previously described threats to their potential
mitigations.
Table 2. Mitigating the threats
| Copyright |
Wrap editions, databases, etc., in Creative Commons
licensing to make and keep them free for everyone to
use, copy, modify, and republish.
|
| Gating |
|
| Technological traps |
|
| Vendor lock-in |
Whatever you build, make it portable. Don't be
beholden to your network and storage hosting, to your
funders, your application developers, or even your
users.
|
Gabler, Hans Walter. "Foreward." 1984. In Joyce, James. Ulysses: A Critical
and Synoptic Edition. Pp. vii-viii.
Groden, Michael, reply by John Kidd. Ulysses Update."
New York Review of Books. February 2, 1989. Vol. 36, No. 1.
URL: https://www.nybooks.com/articles/1989/02/02/ulysses-update/.
Retrieved 25 March 2020.
Joyce, James. Ulysses: A Critical and Synoptic Edition. Ed. Hans
Walter Gabler et al. New York and London: Garland Publishing. 1984. Three
volumes.
Joyce, James. Ulysses Placards [galley proofs]. 1921. MS Eng
160.4. Houghton Library, Harvard University. Digital material. URL: https://iiif.lib.harvard.edu/manifests/view/ids:44067970. Retrieved 25 March
2020.
Kidd, John. "The Scandal of Ulysses." New York Review of Books.
June 30, 1988. Vol. 35, No. 11. URL: https://www.nybooks.com/articles/1988/06/30/the-scandal-of-ulysses-2/.
Retrieved 25 March 2020.
Rossman, Charles. "The New Ulysses: The Hidden Controversy."
New York Review of Books. December 8, 1988. Vol. 35, No. 19.
URL: https://www.nybooks.com/articles/1988/12/08/the-new-ulysses-the-hidden-controversy/.
Retrieved 25 March 2020.
Saint-Amour, Paul K. et. al. "James Joyce: Copyright, Fair Use, and Permissions:
Frequently Asked Questions." "James Joyce Quarterly. Vol. 44, No. 4
(Summer, 2007). Pp. 753-784. Accessed via JSTOR. URL: https://www.jstor.org/stable/25571082. Retrieved 25 March
2020.
Smithies, James. The Digital Humanities and the Digital Modern.
Palgrave Macmillan. 2017.
Staley, Thomas F., John O'Hanlon, and Hans Walter Gabler, reply by John Kidd. "The
Continuing Scandal of ‘Ulysses’: An Exchange." New York Review of
Books. September 29, 1988. Vol. 35, No. 14. URL: https://www.nybooks.com/articles/1988/09/29/the-continuing-scandal-of-ulysses-an-exchange/.
Retrieved 25 March 2020.
Stallman, Richard M. "What is free software?" URL: https://www.gnu.org/philosophy/free-sw.en.html. Retrieved 25 March
2020.
Wikimedia. "File:Creative_commons_license_spectrum.svg example." URL: https://commons.wikimedia.org/wiki/File:Creative_commons_license_spectrum.svg.